In this article we will share understanding UMA policy enforcers with KeyCloak.
1) UMA User resource query
A client is accessing a resource from a resource server
GET /users/alice/album/photo.jpg HTTP/1.1 Host: photoz.example.com
In return, the user will get return of error 401 and the as_uri of the the resource server (where the resource is registered) and a permission ticket
HTTP/1.1 401 Unauthorized WWW-Authenticate: UMA realm="example", as_uri="https://as.example.com", ticket="016f84e8-f9b9-11e0-bd6f-0021cc6004de" …
2) Permission ticket
The permission ticket is as signed jwt which contains the URL and scopes that the user can query/use on this resource.
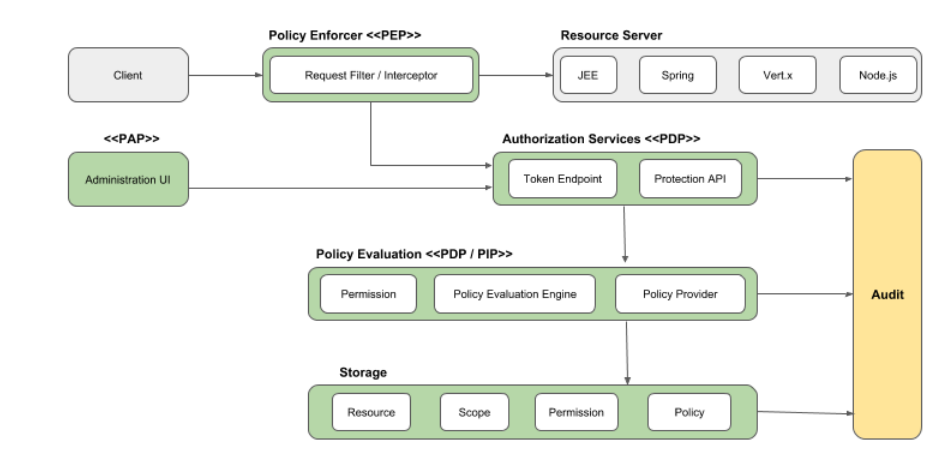
The permission ticket is issued by the keycloak authorization server, through the keycloak PEP (Policy enforcement point). The PEP is teh piece of magic which makes that upon a user call on specific resource is returned as_uri and permission ticket.
3) Policy Enforcement Point
The policy enforcement point act as an inteceptor between the user asking for a resource and the keycloak server.
The Policy enforcer point definition is described in a file keycloak.json, where is indicated for each URL, the default scope that are issued for each HTTP request.
"policy-enforcer": { "enforcement-mode": "PERMISSIVE", "user-managed-access": {}, "paths": [ { "name" : "Album Resource", "path" : "/album/{id}", "methods" : [ { "method": "DELETE", "scopes" : ["album:delete"] }, { "method": "GET", "scopes" : ["album:view"] } ] },
Like this, it is possible to define scopes for HTTP GET, HTTP DELETE …
Those scopes will be retrieved later in the permission ticket and also RPT token.
4) Pointers
- https://www.keycloak.org/docs/latest/authorization_services/index.html#_overview_architecture
- https://www.keycloak.org/docs/latest/authorization_services/index.html#_enforcer_overview
- https://docs.kantarainitiative.org/uma/wg/rec-oauth-uma-grant-2.0.html#client-attempts-tokenless-access
- New Keycloak online training - 19 janvier 2022
- Sizing Keycloak or Redhat SSO projects - 8 juin 2021
- Keycloak.X Distribution - 28 janvier 2021
