Security in the IoT – Internet of Things
Security in the IoT: as the number of Internet connected-devices in any home skyrockets from a few to perhaps even a few hundred, security concerns for this emerging Internet of Things (IoT) will skyrocket too. Studies projects that there will be 50 billion connected devices by 2020; each such node should ideally be protected against malware, spyware, worms, and trojans, as well as overzealous government and commercial interests who themselves might produce their own privacy-compromising intrusions.
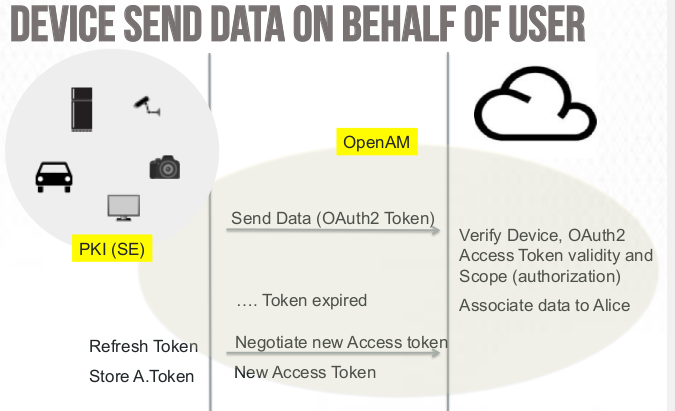
There are both business and technical reasons why the IoT is so difficult to secure. On the technical side, the core problem is that the tried-and-true technologies we use to secure traditional interactions with the Internet just don’t work well – if they work at all. To use Public Key Infrastructure (PKI) technology, for example, each endpoint must be able to store digital keys and run encryption and decryption algorithms, conduct sophisticated handshakes to establish secure SSL connections, etc. However, many IoT nodes like the passive RFID tags simply don’t have the electrical power, storage, or processing power necessary to tackle even the simplest of PKI tasks.
Secondly, a large part of the IoT approach involves machine-to-machine (M2M) communication. In other words, sensors and other IoT endpoints talk to each other, instead of talking to a server somewhere. If your smart thermostat tells your dishwasher when to run, that communication might be running over your home Wi-Fi or perhaps Bluetooth or some other local network protocol that doesn’t require traffic to actually go over the Internet. And not only does it go without saying that Wi-Fi and Bluetooth protocols are shockingly easy to hack, but how are the two communicating nodes supposed to know that the information coming from the other is authorized? Essentially, any kind of M2M interaction requires a certain level of trust, only we have no way of providing that trust in the first place, or revoking it should a breach occur. How will your dishwasher know someone has hacked your thermostat?
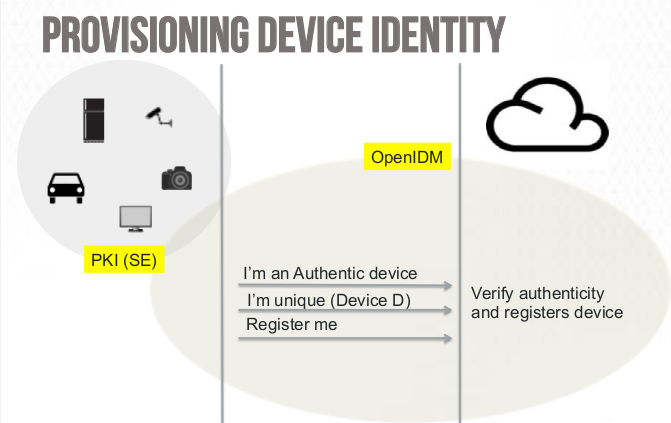
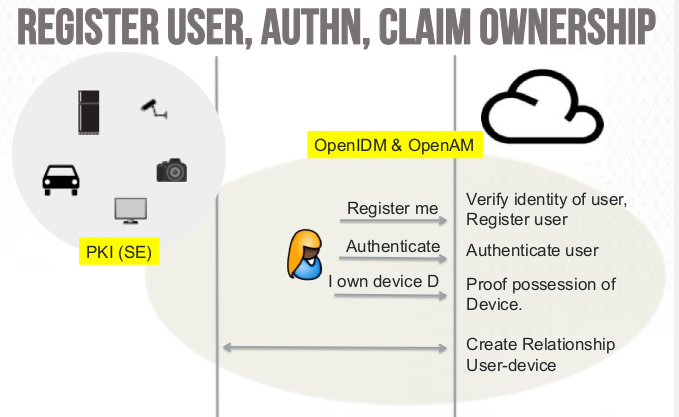
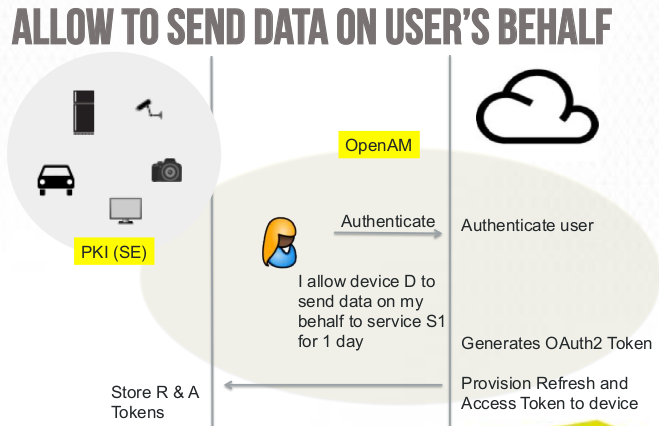
How can we help ? Using and adapting existing technologies and helping building security in the IoT objects design…a few pictures, thanks to Victor Ake from ForgeRock ( you may find the full présentation here) explaining how we could implement Identity Management within the IoT space:
Because IoT is a relatively new field, device developers aren’t as experienced with security principals as existing software companies.
This is also true for device manufacturers, home security system providers, home automation solutions providers, and industrial systems designers—all of whom have never dealt with the threats associated with data security in networked devices.
For over 20 years, PKI-based solutions have been securely exchanging information across the Internet and PKI usage has skyrocketed as companies are protecting more and more data. PKI is already being used to address problems similar to the ones the Internet of Things is likely to experience, as companies are using it to secure devices like mobile phones, tablets, printers, and WiFi hotspots.
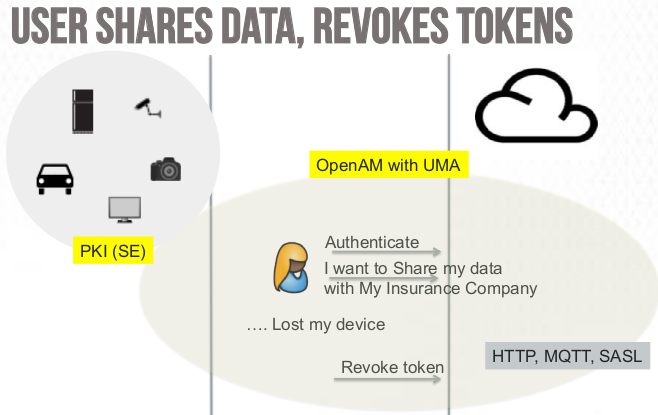
User-Managed Access (UMA) is an OAuth-based protocol that enables an individual to control the authorization of data sharing and service access made by others
UMA defines how resource owners can control protected-resource access by clients operated by arbitrary requesting parties, where the resources reside on any number of resource servers, and where a centralized authorization server governs access based on resource owner policy.UMA can be considered an application of OAuth 2 in that it uses, profiles, and extends OAuth to enable various use cases for resource owner-managed access (the UMA specification calls itself a profile of OAuth 2). UMA’s main flow superficially resembles plain OAuth, and it has embedded subflows that really are instances of ordinary OAuth. While UMA looks OAuth-ish, it functions most like a standardized, API- and scope-aware version of a web access management system — where the policymaker may be an organization as usual, or an individual acting on his or her own behalf.
UMA 2.0 is now a norm and is now « de facto » the solution dedicated for the IoT. the first implementations are up, especially OpenAM 5.5 et RedHat SSO-Keycloak.
A wonderfull presentation of UMA 2.0 :
In short, the UMA protocol lets you add interoperable authorization, access control, privacy, and consent features to your application ecosystem.