Services d’expertise Gestion des Identités et Sécurité Numérique par Open-IAM et Janua.
Découvrez comment Open-IAM (spin-off de JANUA en Aout 2025), fort de son expertise depuis 2004, accompagne ses clients européens à chaque étape de leurs projets de gestion des identités et de sécurité numérique. De l’audit au maintien en condition opérationnelle, notre approche itérative et agile garantit des solutions durables et évolutives. Contactez-nous pour bénéficier de nos services de consulting, intégration, déploiement, support et formation en respectant totalement votre souveraineté numérique.
Depuis 2004, Janua s’est imposé comme un fournisseur de services Open Source de premier plan, offrant un accompagnement complet à ses clients dans la mise en œuvre de leurs projets de gestion des identités et de sécurité numérique. Notre expertise aujourd’hui centrée sur Keycloak, RedHat SSO et LDAP (389DS) couvre l’ensemble du cycle de vie des projets, de l’audit initial au maintien en condition opérationnelle sur le long terme.
Notre approche repose sur des processus itératifs et l’adoption de méthodes agiles/devops, divisées en quatre phases clés :
1. Workshop d’Architecture Technique: Nous collaborons avec vous pour concevoir une solution robuste et évolutive, alignée sur vos besoins actuels et futurs, avec une vision à moyen et long terme sur une période de cinq ans.
2. Maquette ou POC (Proof of Concept): Nous élaborons une maquette ou un POC pour valider les aspects techniques du projet, éliminer les incertitudes et estimer précisément la durée et les coûts associés.
3. Déploiement et Mise en Production: Nous vous assistons dans le déploiement de la solution, en assurant la haute disponibilité, la résilience et en documentant toutes les étapes du processus pour une exploitation fluide.
4. Maintien en Condition Opérationnelle (MCO): Nous assurons le suivi opérationnel de votre système sur plusieurs années, en effectuant les mises à jour nécessaires et en intégrant de nouveaux composants pour garantir sa pérennité.
Nos domaines d’expertise techniques incluent :
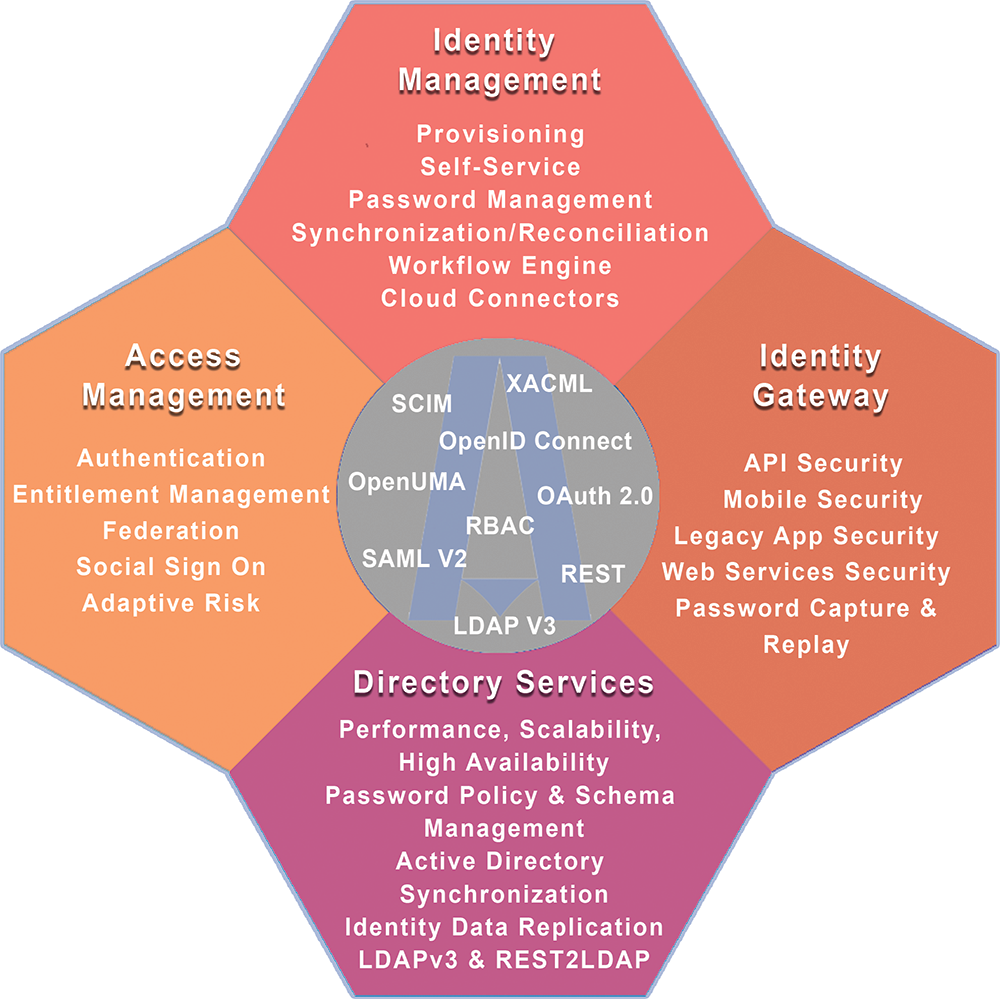
• Audit, Expertise, Consulting, Implémentation, Déploiement et Support de solutions de contrôle d’accès et de gestion des droits avec KeyCloak et RedHat SSO , pour SSO, CDSSO, eSSO, fédération d’identités (SAML V2, OAuth 2.0 & OpenID Connect), et la gestion des annuaires LDAP (OpenLDAP, RedHat DS/389DS).
• Formation sur les outils Open Source de gestion des identités, permettant à vos équipes de monter en compétences et d’exploiter pleinement les fonctionnalités des solutions mises en place.
L’utilisation de composants Open Source de gestion des identités, hébergés par vos soins sur votre infrastructure, ou chez un hébergeur souverain, est un gage de souveraineté numérique pour vos projets de gestion des identités et des accès (IAM).
Contactez-nous dès aujourd’hui pour découvrir comment Open-IAM (Janua.fr) peut vous accompagner dans la mise en œuvre d’une solution pérenne et sécurisée de gestion des identités.
Gestion des identités
Identity & Access Management
Expertise Keycloak - SSO
L’authentification unique, en anglais Single Sign-On ou SSO, est une technique …
SAML, OpenID & Fédération
Security assertion markup language (SAML) et OpenID Connect (OIDC) sont des standards …
La sécurité de l'IOT
Les annuaires LDAP
Services
Intégration & Expertise KeyCloak
Support, intégration et expertise RedHat SSO et Keycloak
Intégration & Expertise RedHat DS
Support, intégration et expertise RedHat DS et 389 DS