An insteresting joint post from Janua and Paradigmo on ForgeRock’s Wiki :
As stated on the OpenStack website, “Keystone is an OpenStack project that provides Identity, Token, Catalog and Policy services for use specifically by projects in the OpenStack family” (https://docs.openstack.org/developer/keystone/). This is very handy as long as by definition, you only need to protect OpenStack APIs and services.
We recently came across a use case where Keystone was only part of the solution. Imagine you have to protect a portal application that includes its own applications and services as well as OpenStack APIs. In this use case, the Keystone framework is not sufficient to provide seamless access control and single sign-on services.
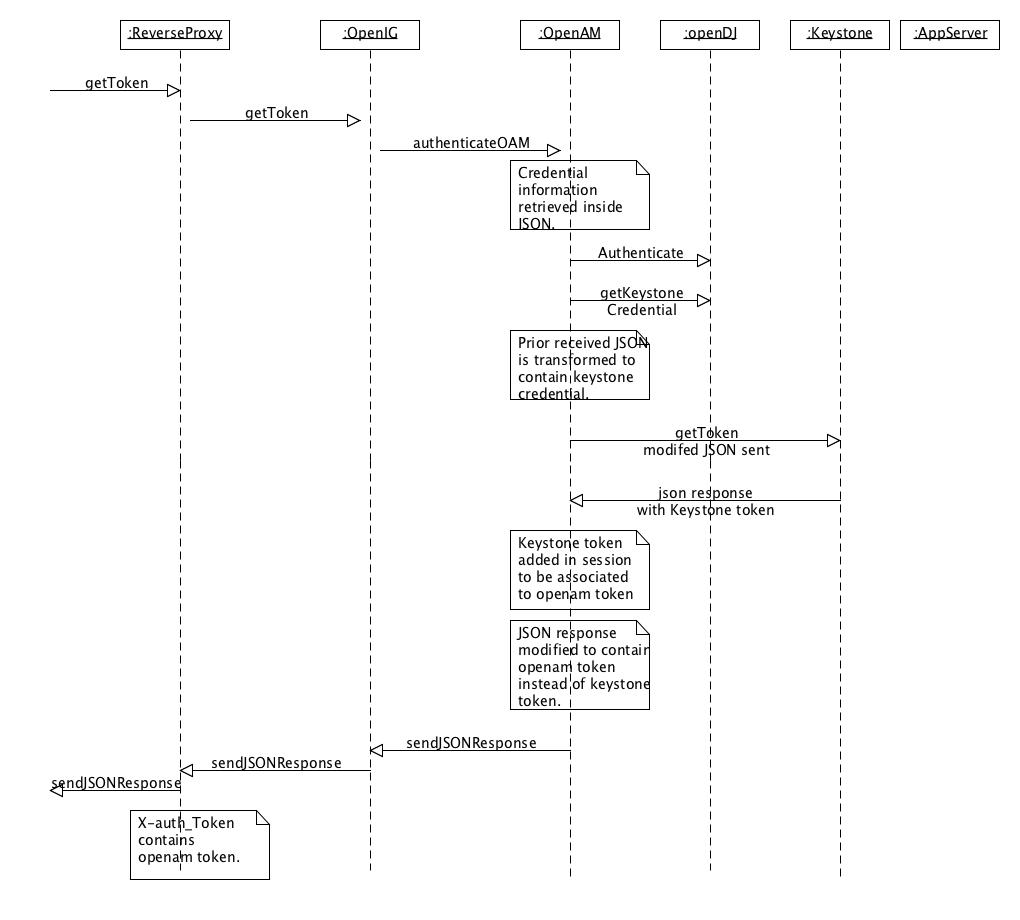
Our implementation consists in front-ending the Keystone service by OpenAM, OpenIG and an OpenAM J2EE agent. The Json enabled client application then needs a single (Json) token delivered by OpenAM in order to access the resources protected both by OpenAM and Keystone.
The whole authentication process is illustrated in the following diagram:
OpenIG is used for its scripting and HTTP headers transformations capabilities. Typcally, OpenAM agents don’t currently support Json, while OpenIG
can be customized to understand Json requests and to return Json formated results.
OpenAM is used :
– to authenticate the user (against an OpenDJ LDAP directory),
– to retrieve his corresponding Keystone credentials stored in his profile,
– to authenticate him against the Keystone server (and thus obtain a valid Keystone token)
– to store the Keystone token in the user’s LDAP entry in OpenDJ.
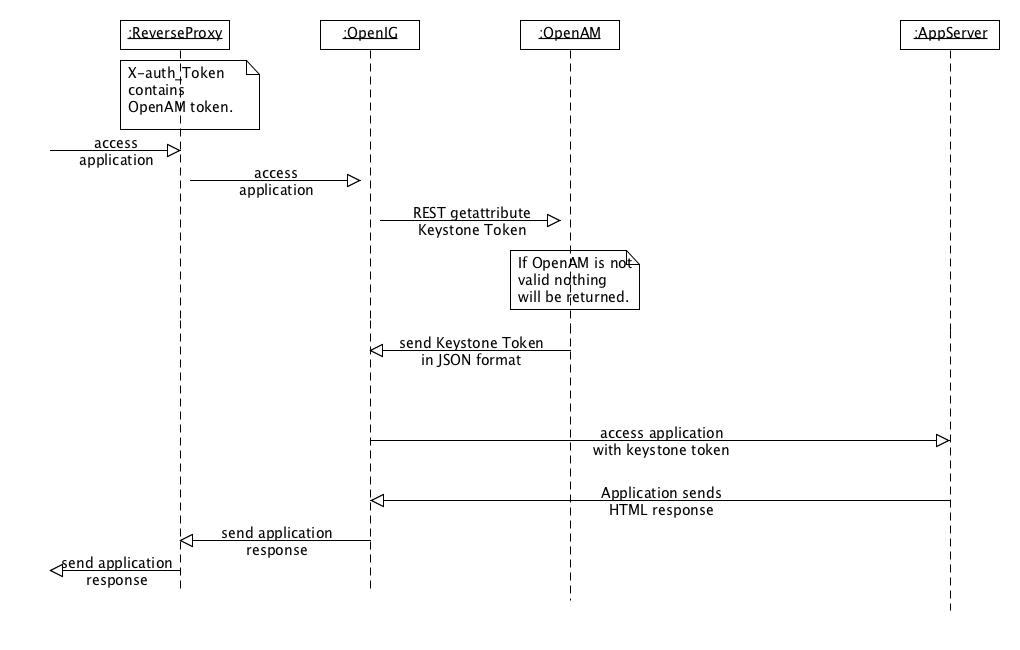
At the end of the authentication process, the response to the user’s initial request contains an OpenAM token, in Json format. When the user accesses resources protected by Keystone, OpenIG’s scripting capabilities are used to retrieve the token from OpenAM and to build a REST call containing a valid Keystone token.
The diagram below depicts subsequent calls by an authenticated client:
Basically, the OpenStack authentication against the Keystone server is achieved by OpenAM itself, thanks to a specialized authentication module. This architecture leverages OpenAM authentication framework and API’s and also benefits from OpenAM session failover feature if enabled. It also makes it easier to store and retrieve Keystone tokens than if it’d been implemented on the OpenIG side.
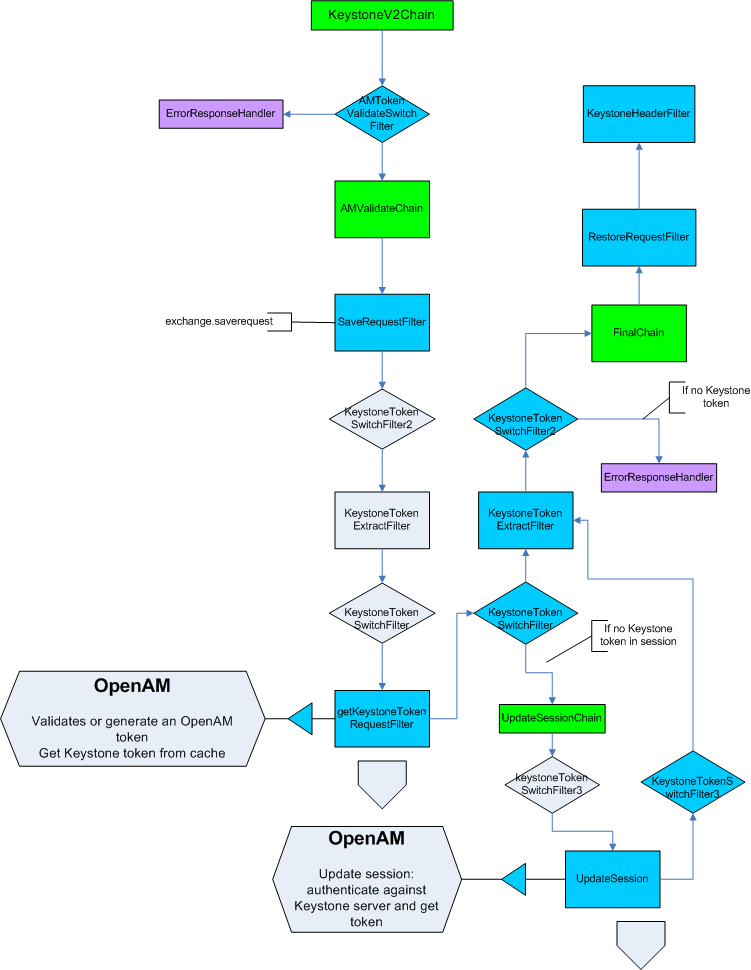
The diagram below depicts what happens in OpenIG internally:
- New Keycloak online training - 19 janvier 2022
- Sizing Keycloak or Redhat SSO projects - 8 juin 2021
- Keycloak.X Distribution - 28 janvier 2021