Mapping LDAP Group and Roles to RedHat SSO Keycloak : the goal of this article is to showcase how it is possible to expose and to use LDAP roles at keycloak level.
This feature will illustrated by creating new users which belong to the ldap-admin group. Those new users will get assigned automatically the keycloak admin role as effective role, and hence will be abel to connect to the keycloak master console realm as new admins.
LDAP Group to keycloak Roles mapping workflow
This is going to be illustrated with the following use case:
- (1) Only keycloak admin roles, can log to the keycloak admin console
- (2) In the following an ldap-admin group is created (LDAP level).
- (3) This ldap-admin group is mapped at SSO level to a ldap admin group using ldap group mapper extension
- (4) At SSO level, the ldap-admin group has got a list of available roles. The admin role is picked as assigned role of this group.
- (5) As a consequence, it means that any user which belongs to the ldap-admin group (LDAP level) is going to have following properties when synchronized at SSO level
- It will be part of the ldap-admin group (SSO level)
- it will get automatically assigned the roles of the ldap-group (I.e an admin role)
Concrete application: creating an ldap/SSO admin
Such a feature is very interesting, as this allows to create users and attach to them the relevant SSO property that you want to be exposed at SSO level.
For example, let’s assume that you want to create some users, that you can promote or demote as admin users. Providing such a feature with the above workflow in place is very easy, as you only need to add/remove the ldap-admin group membership at ldap level for a given user.
It means that any user which is part of such a group will be automatically assigned admin roles and hence able to log to the admin consoel as administrator.
Use case example
Example requirements
The use case example is based using the ldap test case provided in keycloak examples/ldap suite
Installing keycloak example ldap
To install the keycloak example example, you need to:
• (1) clone/download the latest of keycloak examples
https://github.com/keycloak/keycloak/archive/master.zip
• (2) compile keycloak example
Unzip mater.zip
cd keycloak-master
cd keycloak-master
• (3) Launch keycloak embedded LDAP server
mvn exec:java -Pldap
An embedded apache studio is spawned on :
- localhost port 10389
- BindDN Credentials:
- uid=admin,ou=system/password
Connecting with Jexplorer to the embedded LDAP server
The user needs to enter following credentials in jexplorer to connect to the embedded ldap server.
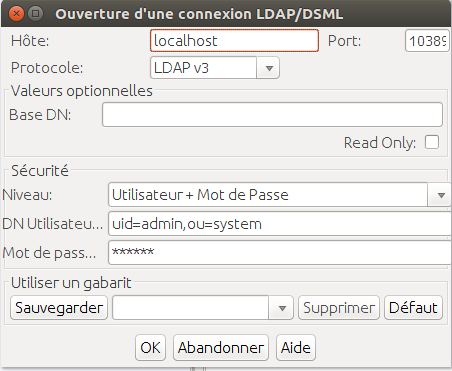
Browsing the embedding ldap
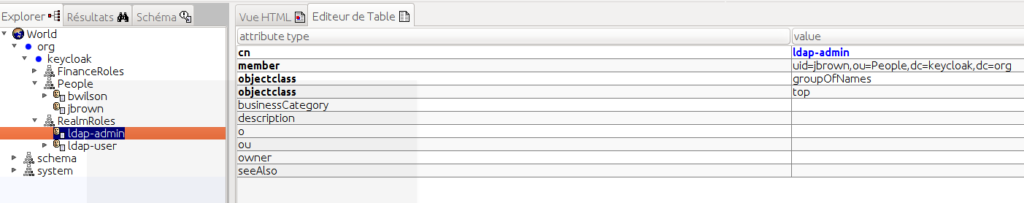
Jexplorer allows to display the embedded LDAP DIT.
Some points of importance to be noticed:
- (1) users are located below : ou=people,dc=keycloak, dc=org
- admin users are part of the ldap-admin group
- ldap-admin is defined by the dn: cn=ldap-admin,ou=RealmRoles, dc=keycloak,dc=org
- ldap-admin group membership is defined by adding the member attribute with the user dn (here: uid=jbrown, ou=people,dc=keycloak,dc=org)
User Federation with Ldap
Setting up ldap user federation connector
User Federation agreement has to be put in place as mentioned below
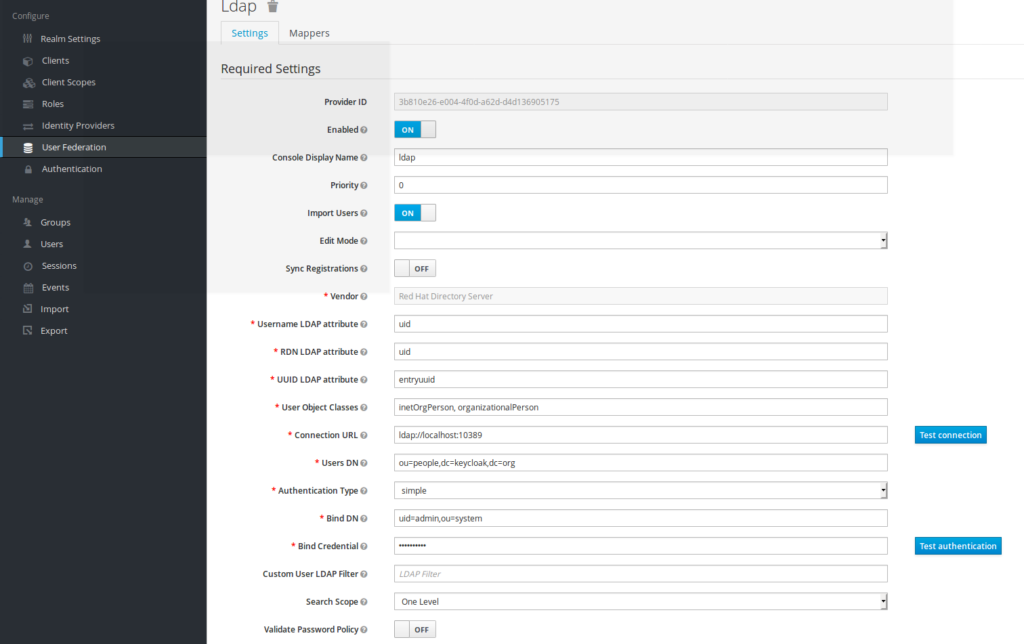
The information to be put are:
- Vendor: Redhat Directory Server
- Usermame LDAP attribute: uid
- RDN LDAP attribute: uid
- UUID LDAP attribute: entryuuid
- User Object Class: inetOrgPersonn
- ConnectionUrl ldap://localhost:10389
- Users DN: ou=people,dc=keycloak,dc=org
- Authentication:simple
- Bind DN: uid=admin,ou=system
- password:secret
Defining LDAP synchronisation
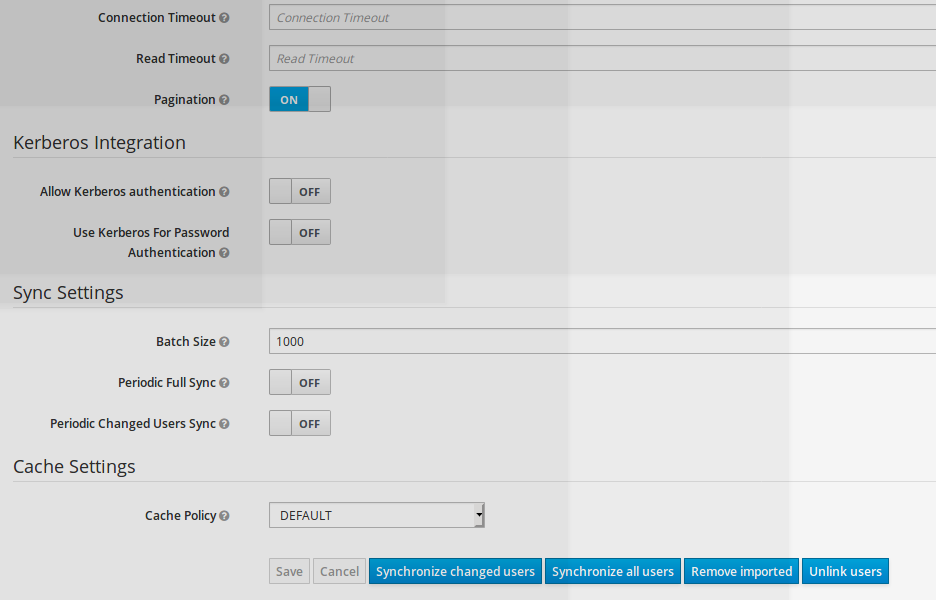
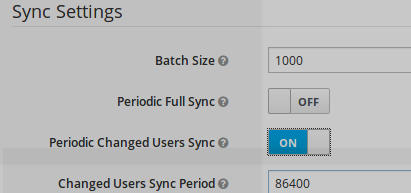
As soon as LDAP connector for user federation is in place, one has to define LDAP-SSO Synchronization mecanism.
Synchronisation can be defined:
- on demand (by clicking on synchronize all users or synchronize changed users button)
- Periodic Full Sync
- Periodic changed Users Sync (on given time frame)
Adding group ldap mapper
Creating ldap group mapping
A ldap mapper is created, on this user federation connector
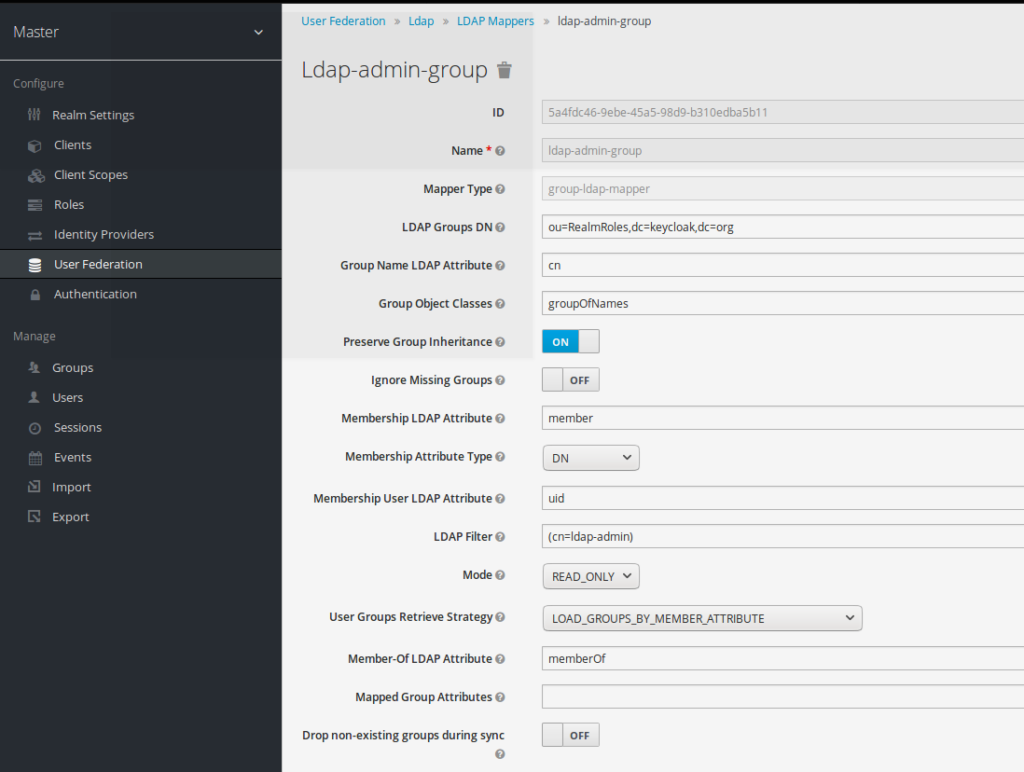
This ldap-admin-group has to be created with following mapping properties:
- Mapper Type:
- group-ldap-mapper (this the property to be selected when creating this new ldap mapper)
- Ldap group DN:
- ou=realmRoles,dc=keycloak,dc=org
- LDAP filter
- cn=ldap-admin
For all the other mapping fields, the default value is taken as mentioned above
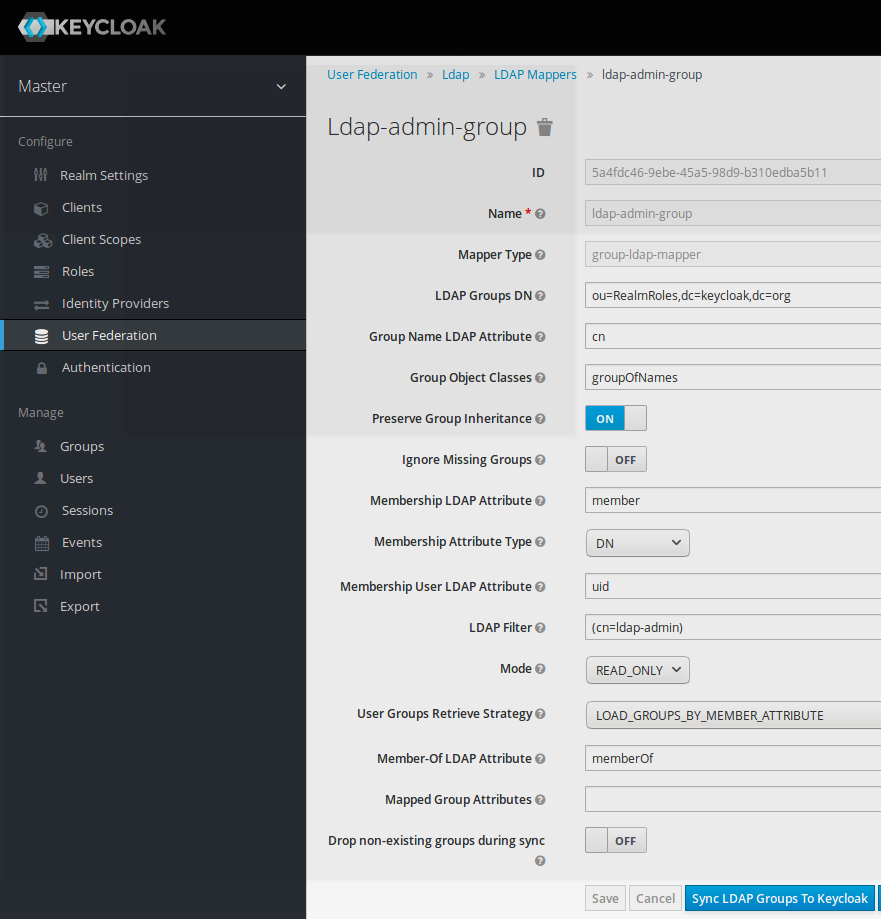
Synchronizing ldap group mapping
Now, as the ldap group mapper is in place, it is possible to synchronize it to the SSO.
- click on button “Sync LDAP Groups to keycloak”
Adding SSO Role to keycloak group
Keycloak ldap-admin group
LDAP group (ldap-admin) can now be seen at Keycloak SSO level after group synchronization performed previously.
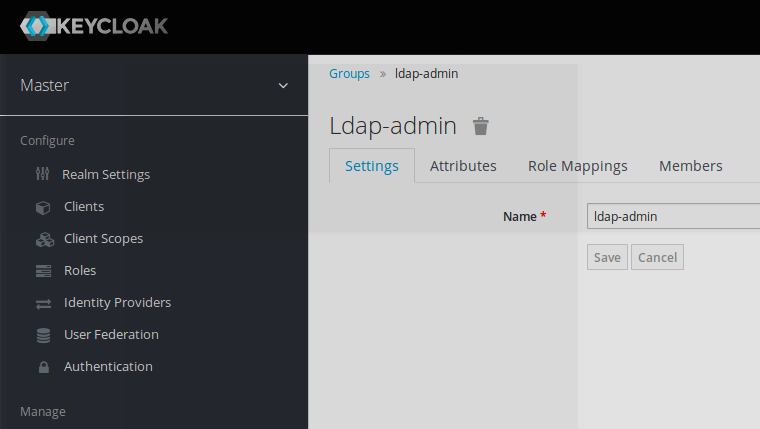
Adding a Keycloak role to this ldap-admin group
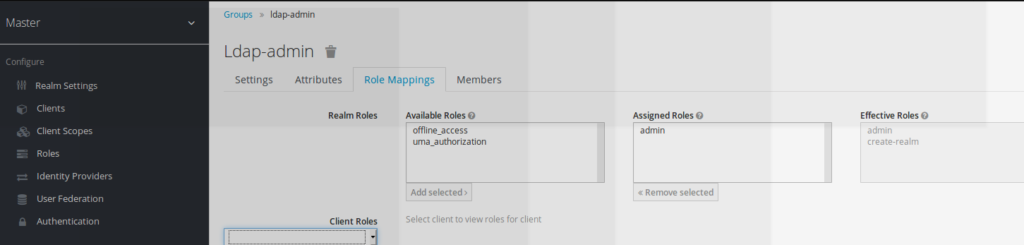
The keycloak admin role is assigned as effective roles to this ldap-admin group.
As a consequence, it means that any user which belongs to the ldap-admin group will be automatically assigned the keycloak admin role which allows him to connect to the admin console
Testing workflow
Creation of a new ldap user
A new user is created (orivat/password) at LDAP level
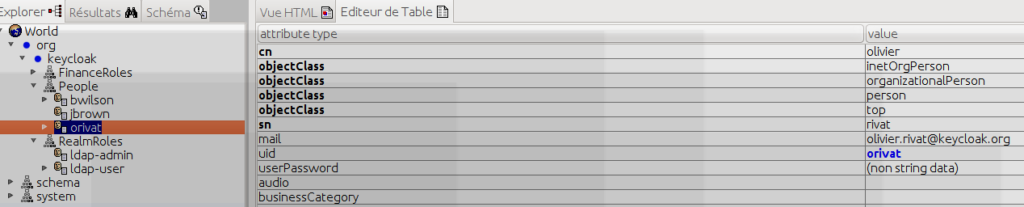
Ldap-user part part of ldap-admin group
The entry uid=orivat,ou=People,dc=keycloak,dc=org is added as being part of the member ldap-admin group.
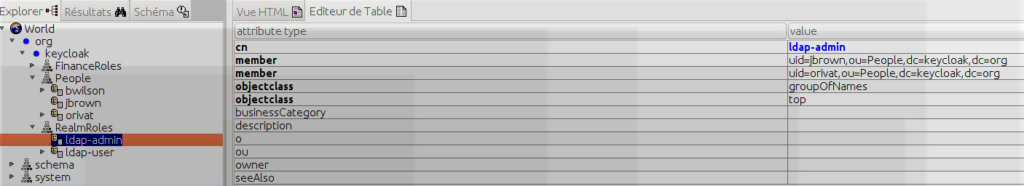
Keycloak ldap synchronization
The new ldap user orivat now can be retrieved at keycloak SSO level.
(Synchronization can be achieved by defining periodic sync, or on demand sync as seen before)
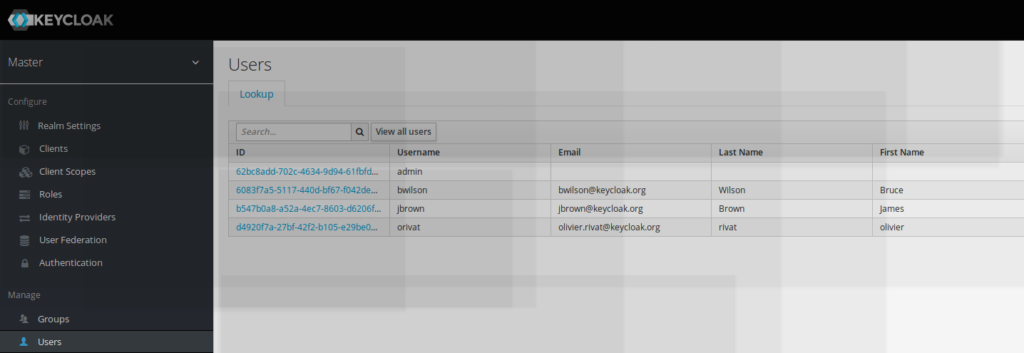
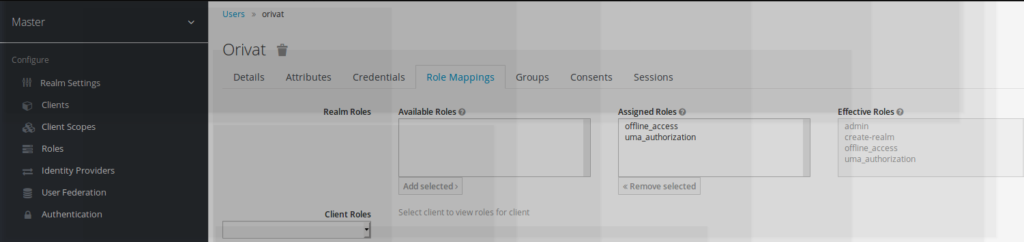
new user with keycloak role admin rights
As mentioned ldap-admin rights have been added to the new user created.
Due to the keycloak ldap-admin group mapping, the new user gets also automatically assigned keycloak effective admin rights
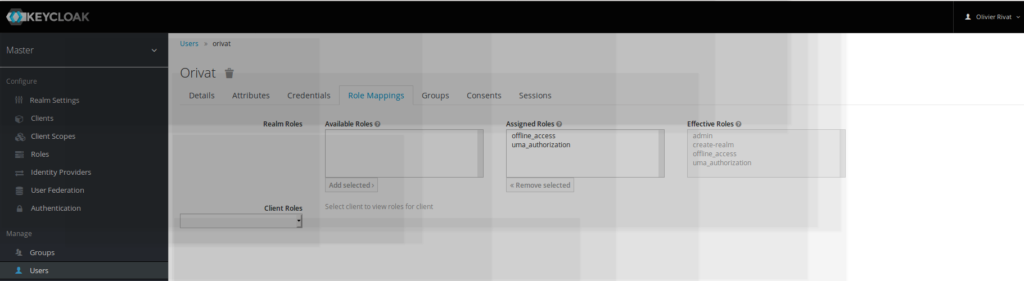
Logging to the admin console with a new admin user-basis
Irt is now possible to log to keycloak admin console with a new user different from admin, as this new user has got also the admin rights.
- New Keycloak online training - 19 janvier 2022
- Sizing Keycloak or Redhat SSO projects - 8 juin 2021
- Keycloak.X Distribution - 28 janvier 2021
