This article is the sequel of the theoretical and architecture Saml 2.0 openam presentation published a few days ago. In this new article, you will learn practically how to build an OpenAM Saml configuration.
1) Presentation
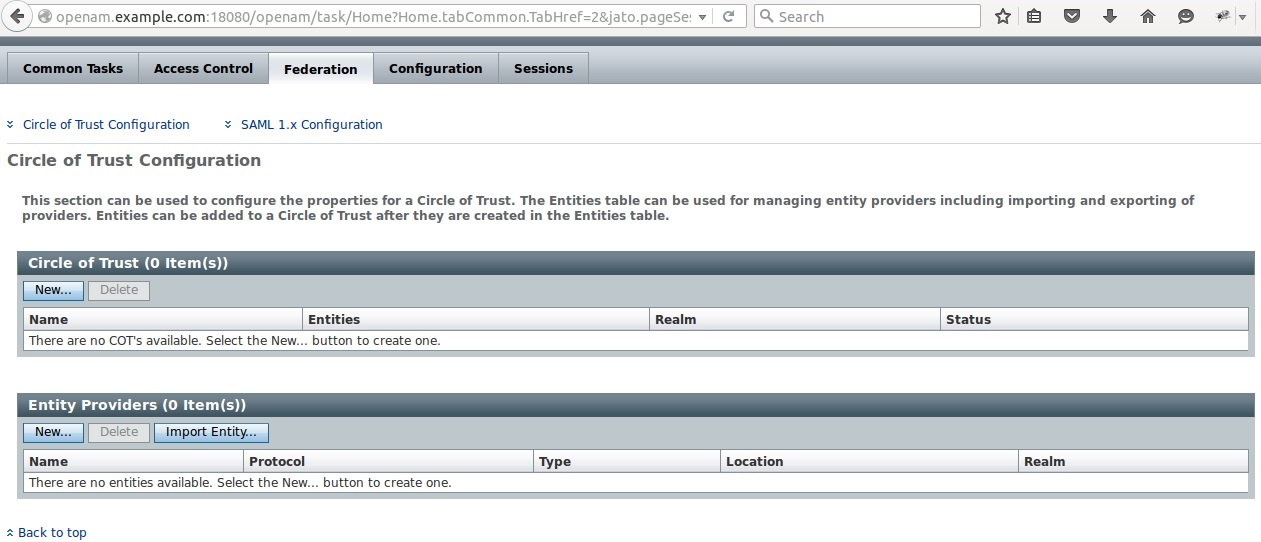
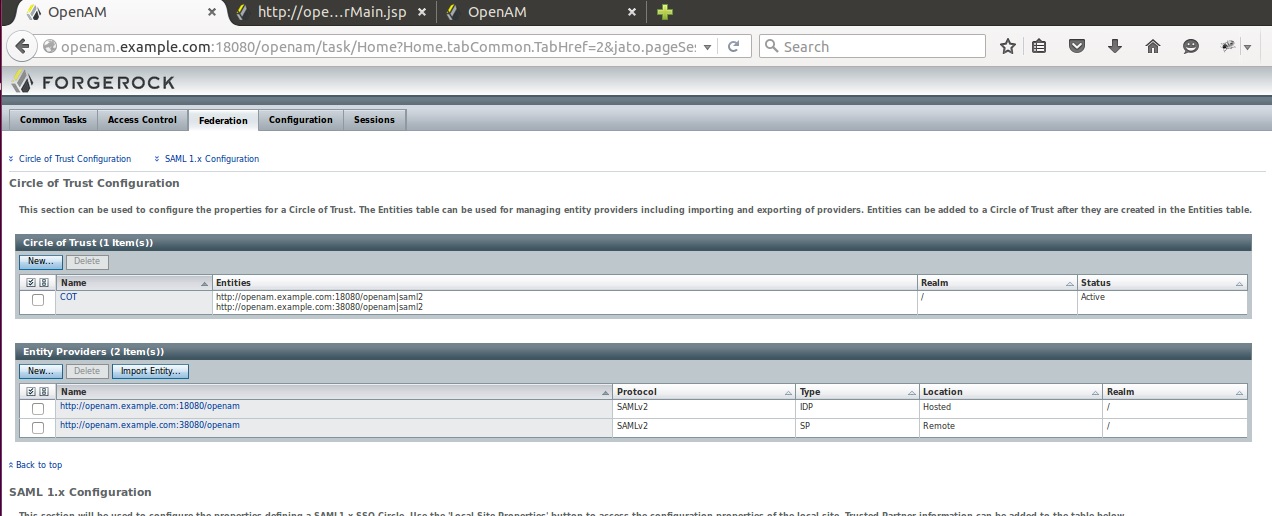
This document describes how to use openAM12 to perform SAML configuration. The SAMLV2 configuration is illustrated throughout 2 instances :
- idp :
- sp :
The penultimate goal is to provide Federation between the both instances. Upon startup, the Federation section is empty.
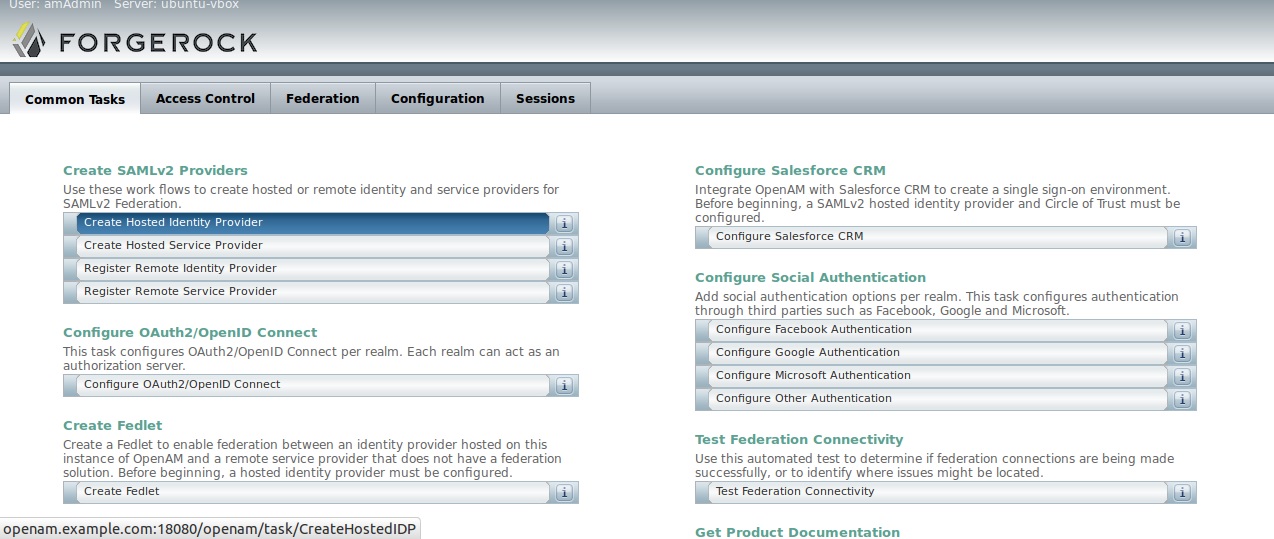
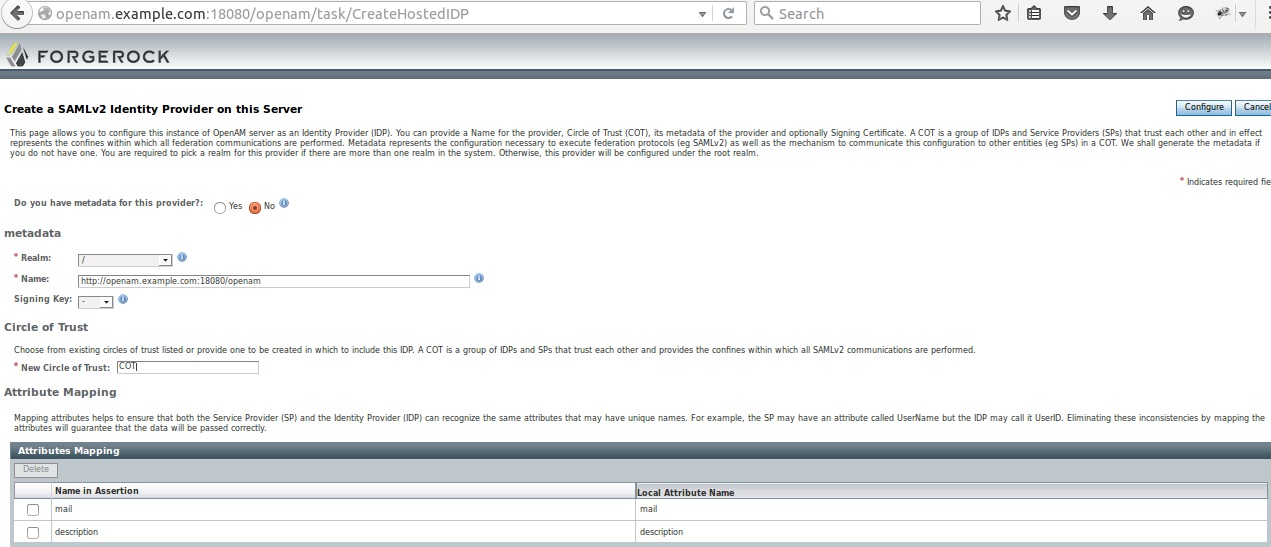
2) IDP creation
Le’s create a IDP
2.1) Host IDP verification
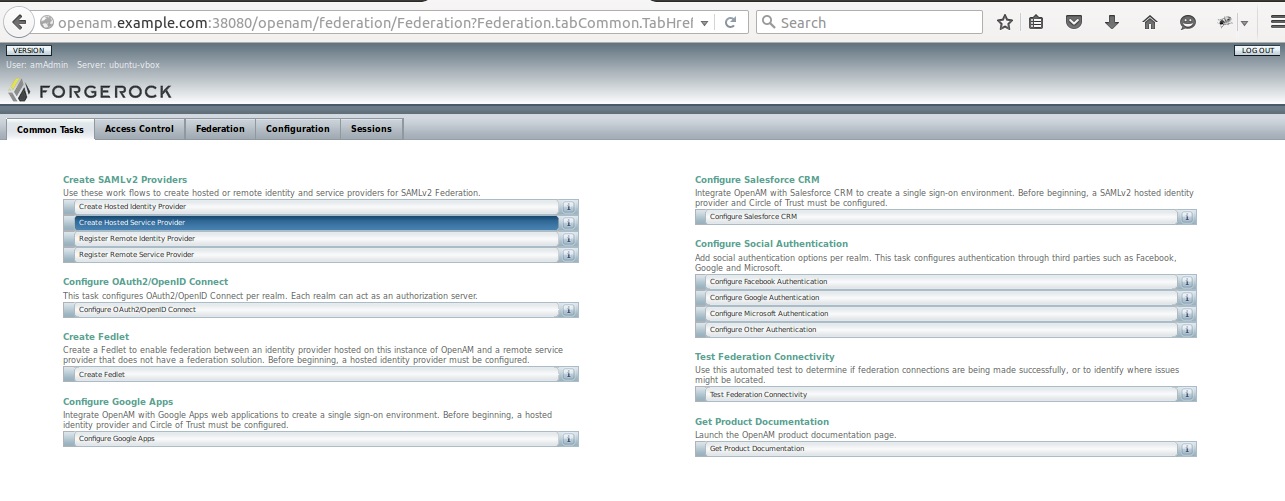
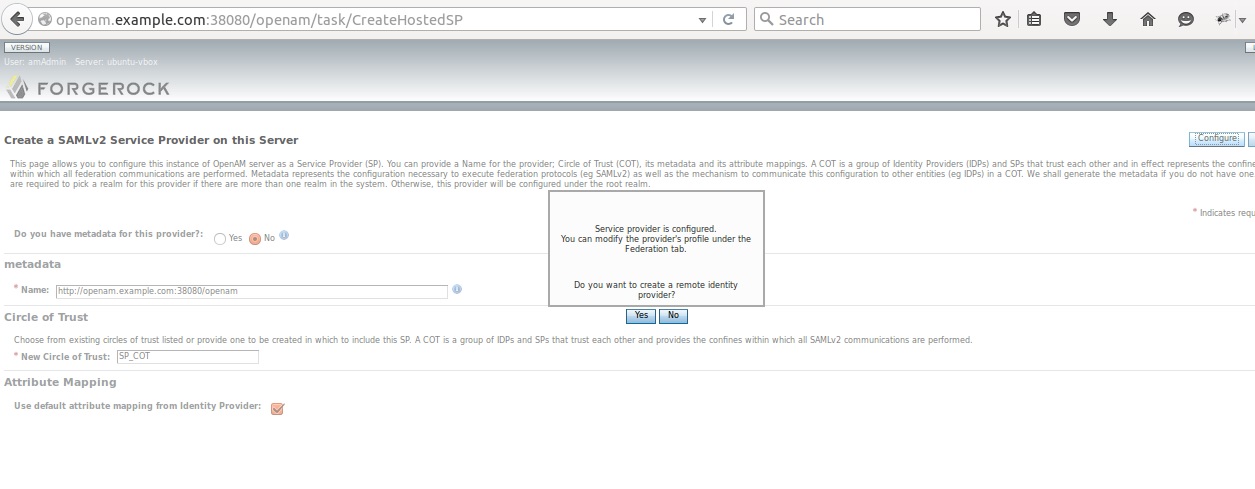
3) SP Creation
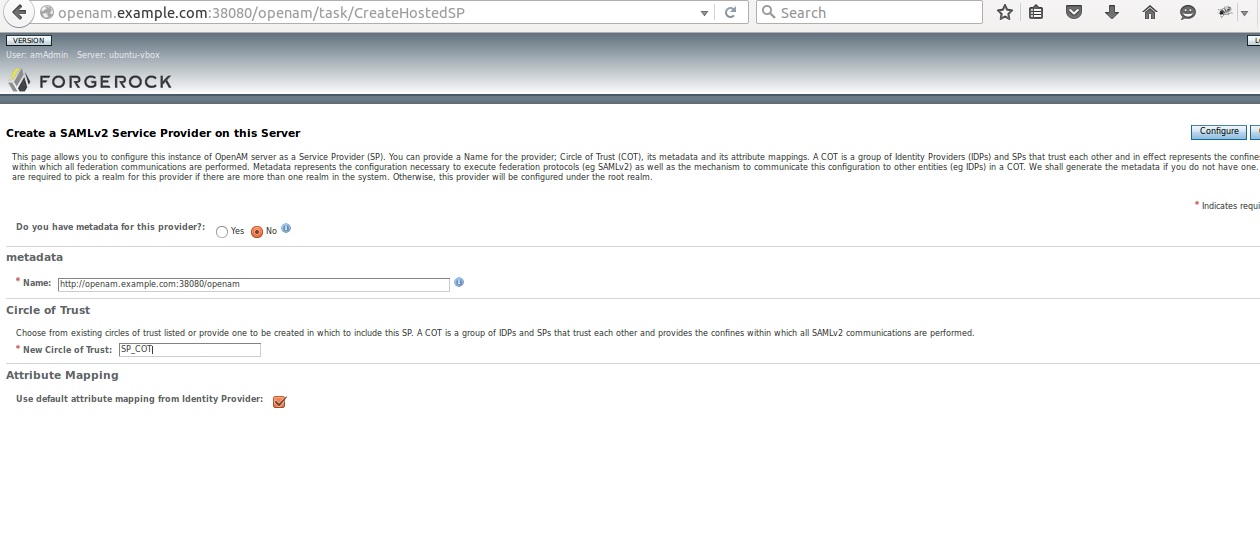 3.1) Service Provider Configuration
3.1) Service Provider Configuration
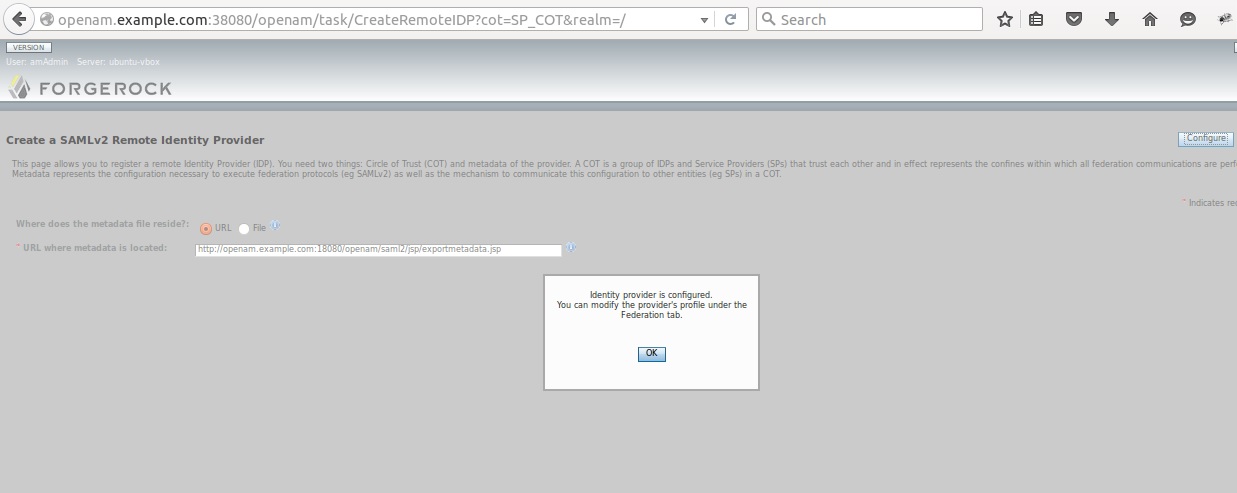
The remote IDP is cretaed on SP host using IDP XML metadata
3.3) Remote Identity Provide Verification
4.2) Remote Service Provider (creating from IDP)
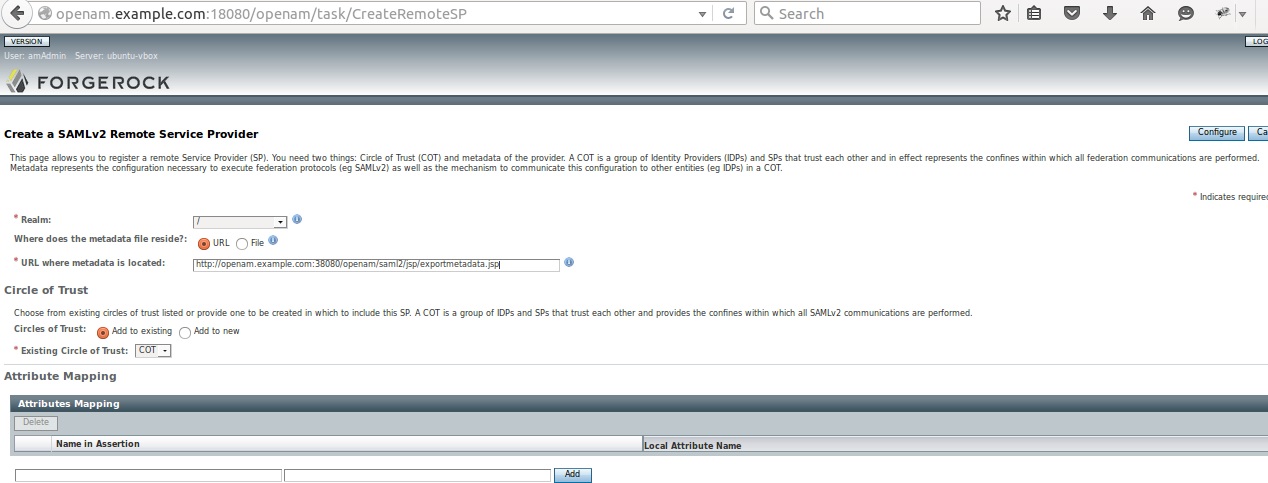
4.3) Remote Service Provide Creation
The remote Service provider at IDP level is created using SP XML metadata.
4.3) Verification at IDP of Cicle of Trust
The Circle of Trust contains both teh IDP and the remote SP
5) SSOInit Request
Once the federation has been configured, the SSO initilisation can be configured either from SP or IDP using either idpSSOInit.jsp or spSSOInit.jsp.
5.1) SSOInitRequest from IDP
5.2 ) SSOInit Request from SP
6)Example
6.1) SAML AUTH Request
<samlp:AuthnRequest xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" ID="s2c51ed68e25fcd63274509c62410e76280ba3e9d0" Version="2.0" IssueInstant="2016-11-02T21:42:15Z" Destination="https://openam.example.com:18080/openam/SSORedirect/metaAlias/idp" ForceAuthn="false" IsPassive="false" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" AssertionConsumerServiceURL="https://openam.example.com:38080/openam/Consumer/metaAlias/sp" > <saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">https://openam.example.com:38080/openam</saml:Issuer> <samlp:NameIDPolicy xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" Format="urn:oasis:names:tc:SAML:2.0:nameid-format:persistent" SPNameQualifier="https://openam.example.com:38080/openam" AllowCreate="true" /> <samlp:RequestedAuthnContext xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" Comparison="exact" > <saml:AuthnContextClassRef xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef> </samlp:RequestedAuthnContext> </samlp:AuthnRequest>
6.2) SAML AUTH Response
<samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" ID="s2e72f901467b54ba311de809d99f849635b8b4fb6" InResponseTo="s2c51ed68e25fcd63274509c62410e76280ba3e9d0" Version="2.0" IssueInstant="2016-11-02T21:42:48Z" Destination="https://openam.example.com:38080/openam/Consumer/metaAlias/sp" > <saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">https://openam.example.com:18080/openam</saml:Issuer> <samlp:Status xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"> <samlp:StatusCode xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" Value="urn:oasis:names:tc:SAML:2.0:status:Success" /> </samlp:Status> <saml:Assertion xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" ID="s2d1ee506939c9626fbb69d1b958a8ce5e38e43150" IssueInstant="2016-11-02T21:42:48Z" Version="2.0" > <saml:Issuer>https://openam.example.com:18080/openam</saml:Issuer> <ds:Signature xmlns:ds="https://www.w3.org/2000/09/xmldsig#"> <ds:SignedInfo> <ds:CanonicalizationMethod Algorithm="https://www.w3.org/2001/10/xml-exc-c14n#" /> <ds:SignatureMethod Algorithm="https://www.w3.org/2000/09/xmldsig#rsa-sha1" /> <ds:Reference URI="#s2d1ee506939c9626fbb69d1b958a8ce5e38e43150"> <ds:Transforms> <ds:Transform Algorithm="https://www.w3.org/2000/09/xmldsig#enveloped-signature" /> <ds:Transform Algorithm="https://www.w3.org/2001/10/xml-exc-c14n#" /> </ds:Transforms> <ds:DigestMethod Algorithm="https://www.w3.org/2000/09/xmldsig#sha1" /> <ds:DigestValue>OiNkgebOd6FrTjeOGS+dVrvNj0c=</ds:DigestValue> </ds:Reference> </ds:SignedInfo> <ds:SignatureValue> XMisHXQkhCsT2kU1+p6jsZ9txcsQZu8rXf7eMtumnk/1CY2SeHtkXfj0Xdxa1xJY1Mo6MqzHU20B 2pmUGbrd1m0QYw/L+rwJRH5OMpQKjwoGycHyENT2H/gP0O8jFt+SYicee57WcPFAi3QDvCyZwgyi t36AIRv3xQNWfc7tImo= </ds:SignatureValue> <ds:KeyInfo> <ds:X509Data> <ds:X509Certificate> MIICQDCCAakCBEeNB0swDQYJKoZIhvcNAQEEBQAwZzELMAkGA1UEBhMCVVMxEzARBgNVBAgTCkNh bGlmb3JuaWExFDASBgNVBAcTC1NhbnRhIENsYXJhMQwwCgYDVQQKEwNTdW4xEDAOBgNVBAsTB09w ZW5TU08xDTALBgNVBAMTBHRlc3QwHhcNMDgwMTE1MTkxOTM5WhcNMTgwMTEyMTkxOTM5WjBnMQsw CQYDVQQGEwJVUzETMBEGA1UECBMKQ2FsaWZvcm5pYTEUMBIGA1UEBxMLU2FudGEgQ2xhcmExDDAK BgNVBAoTA1N1bjEQMA4GA1UECxMHT3BlblNTTzENMAsGA1UEAxMEdGVzdDCBnzANBgkqhkiG9w0B AQEFAAOBjQAwgYkCgYEArSQc/U75GB2AtKhbGS5piiLkmJzqEsp64rDxbMJ+xDrye0EN/q1U5Of+ RkDsaN/igkAvV1cuXEgTL6RlafFPcUX7QxDhZBhsYF9pbwtMzi4A4su9hnxIhURebGEmxKW9qJNY Js0Vo5+IgjxuEWnjnnVgHTs1+mq5QYTA7E6ZyL8CAwEAATANBgkqhkiG9w0BAQQFAAOBgQB3Pw/U QzPKTPTYi9upbFXlrAKMwtFf2OW4yvGWWvlcwcNSZJmTJ8ARvVYOMEVNbsT4OFcfu2/PeYoAdiDA cGy/F2Zuj8XJJpuQRSE6PtQqBuDEHjjmOQJ0rV/r8mO1ZCtHRhpZ5zYRjhRC9eCbjx9VrFax0JDC /FfwWigmrW0Y0Q== </ds:X509Certificate> </ds:X509Data> </ds:KeyInfo> </ds:Signature> <saml:Subject> <saml:NameID Format="urn:oasis:names:tc:SAML:2.0:nameid-format:persistent" NameQualifier="https://openam.example.com:18080/openam" SPNameQualifier="https://openam.example.com:38080/openam" >zNhpWD1UJuh46KtbJyr9lXWB3qJ5</saml:NameID> <saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"> <saml:SubjectConfirmationData InResponseTo="s2c51ed68e25fcd63274509c62410e76280ba3e9d0" NotOnOrAfter="2016-11-02T21:52:48Z" Recipient="https://openam.example.com:38080/openam/Consumer/metaAlias/sp" /> </saml:SubjectConfirmation> </saml:Subject> <saml:Conditions NotBefore="2016-11-02T21:32:48Z" NotOnOrAfter="2016-11-02T21:52:48Z" > <saml:AudienceRestriction> <saml:Audience>https://openam.example.com:38080/openam</saml:Audience> </saml:AudienceRestriction> </saml:Conditions> <saml:AuthnStatement AuthnInstant="2016-11-02T21:42:47Z" SessionIndex="s2a74f501df0ad5c41e1d3c04174641673794fa601" > <saml:AuthnContext> <saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef> </saml:AuthnContext> </saml:AuthnStatement> </saml:Assertion> </samlp:Response>
7) Pointers
Below are some interesting pointers :
- Presentation of SAMLV2 configuration
- Presentation of remote SP performing anonymous bind
- Other pointers
- New Keycloak online training - 19 janvier 2022
- Sizing Keycloak or Redhat SSO projects - 8 juin 2021
- Keycloak.X Distribution - 28 janvier 2021