In this article, janua’s CTO shares tips and tricks regarding access token security with Keycloak.
1. Description
Tokens are issued to clients by an authorization server with the approval of the resource owner. The client uses the access token to access the protected resources hosted by the resource server.
The usual well-known Oauth2 authentication are available with keycloak
- Authorization code
- Implicit flow
-
Direct Access Grant (Resource owner password
credential)
2. Keycloak Access Token Security Consideration
Access token allows a client to access to other
resources.
Not only is an access token very precious as it
allows to access to other resources, but it may contain also very
sensitive information, such as roles, claims ….
In keycloak, the format of an access token is a signed JWT, in clear text. Even if the access token is no longer valid, being able to access such strategic can represent a major a security breach.
It means that if a malicious is able to gain access to the keycloak access token, he can get access to very sensitive data of your company.
3. Safeguards to put in place to use and protect keycloak access token
-
1st safeguard : Using Encryption
-
The traffic has to be always encrypted
(TLS/HTTPS).
The Keycloak access token (JWT format) will never get exposed - This Oauth2/openid spec already mentions this , but always good to remember
-
The traffic has to be always encrypted
(TLS/HTTPS).
-
2nd Safeguard :
- Use Authorization code flow, as the access token is only known from the client
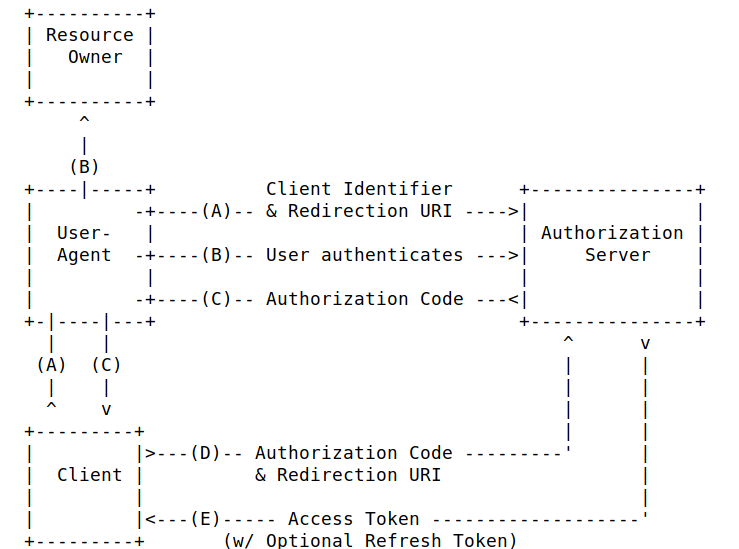
Like this, the access token gets never exposed to the outside
3. Authentications flows which are at risk
- Implicit mode Oauth2 authentication flows such as Implicit mode is at risk, as the access_token is directly passed to the resource Agent (i.e browser)
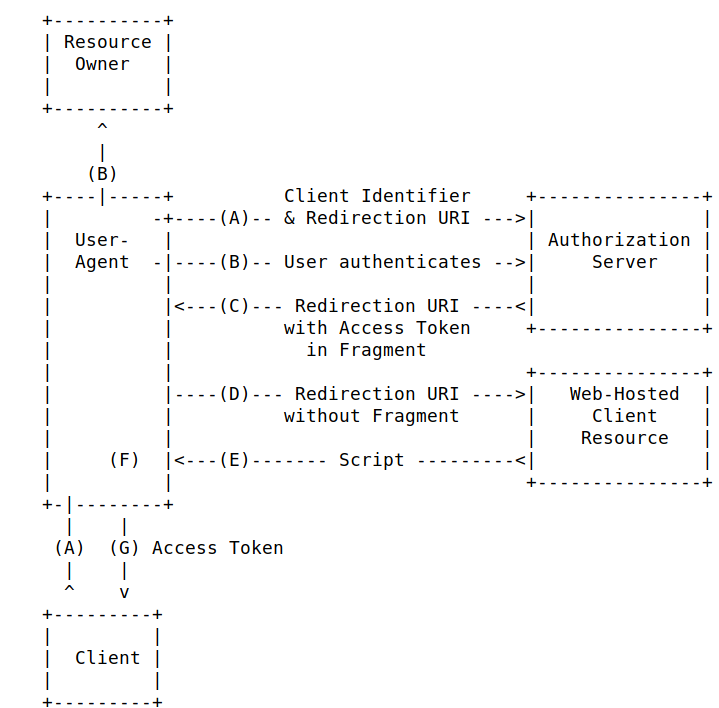
- Direct access grant (Read only password credentials)
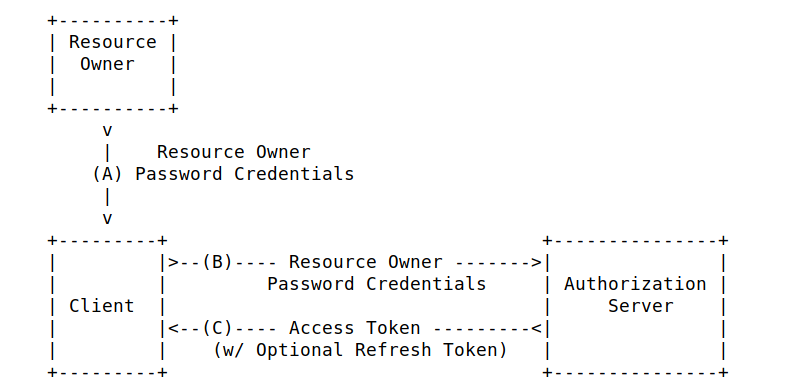
4. Synthesis – Hardening for keycloak Access Token
In keycloak access tokens are of signed JWT format, and may expose very sensitive piece of information (roles, claims).
Access token encryption is not available for keycloak and could potentially be exposed (cf above), which could represent a security breach.
The safeguards to put in place to prevent keycloak access token exposure to the outside world are :
-
(1) Traffic always encrypted
- provides confidentiality
-
(2) Use only Authorization code mode
- The token is never to the user agent (i.e browser)
- (3) Disable Direct access grant (read only password credential)
-
(5) Do not use implicit authentication flow
- (access token will never get exposed to the user agent)
As a conclusion, it is possible to put in place a
robust secure infrastructure with keycloak, when following the above
guidelines
- New Keycloak online training - 19 janvier 2022
- Sizing Keycloak or Redhat SSO projects - 8 juin 2021
- Keycloak.X Distribution - 28 janvier 2021
